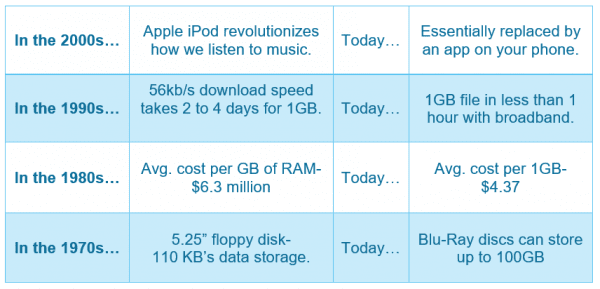
It seems there is a near constant evolution that takes place in regards to technology. Notable breakthroughs seem to happen in the industry every year, as consumerism empowers companies to spend billions developing the “next big thing.” Just take a look at some of the things that have changed over the last 55 years…

It’s just a password—what’s the big deal?
A password presents a single obstacle that, when overcome, could put someone on the fast-track to your personal and financial information. So it would make sense to strengthen this defense, right? Using a password as the only access control is a weak defense, but luckily it is a risk that can be easily mitigated.
Is my password secure?
Personal data
As a consumer, you trust the security of your personal data to the entities hosting those accounts. Whether it is online banking, social media, retail or the Nickelback fan club (seriously, this is a thing?), you are at the mercy of the organization’s selected level of security. To combat this, the rule of thumb should be to utilize the highest security level available. That means creating a complex (upper/lowercase, numbers and symbols) password with at least 10 characters, or the maximum available.
You definitely should NOT use “password” or “123456” as your password. You might be thinking, “Who would actually do that?” Well, they have only been the most popular passwords 5 years running.
Encrypted password lists are often stolen in bulk, sometimes millions at a time. A hacker will aim to decrypt as many passwords as possible from the list in a short amount of time. The stronger your password is, the better chance your data remains safe. Still not convinced? See for yourself how long it would take to decrypt various passwords. Spoiler alert: “Zf3!gg4$” could theoretically be cracked in just over a minute.
Business
When it comes to your business, you should have more control over the security level. Implementing Two-Factor Authentication is a practical way to protect your data. This means you need to present something you know (a password) and either something you have (a key fob/access card) or something you are (fingerprint). It’s essentially the same concept as locking both the handle and the deadbolt of your front door before leaving for vacation.
Password alternatives…from prints to portraits
Cybersecurity folks are working to develop secure alternatives to the password. Take a look at some options in the pipeline. I’ve included some with actual potential, and one that seems to be a little more focused on appealing to younger generations than finding a realistic solution.
- Biometrics have been around for a while, but with various pros and cons. As designs have improved and costs have lowered, they have slowly become more mainstream. But biometrics are still just a variant of single factor authentication.
 It also introduces the risk of burning your finger on the stove and subsequently losing access to your computer for three days. It is still a solid option, though, when paired with a password or other factors. Plus, entering a room after a retina scan will legitimately make you feel super important and give you secret agent vibes.
It also introduces the risk of burning your finger on the stove and subsequently losing access to your computer for three days. It is still a solid option, though, when paired with a password or other factors. Plus, entering a room after a retina scan will legitimately make you feel super important and give you secret agent vibes. - With hardware-based device authentication, you can turn your personal laptop into its own password. A unique “fingerprint” from the device is paired with a user password to provide more security and control for a business. If someone takes the device but does not have the password, then network access would be disabled. Conversely, if someone steals the account password, it will prove useless unless entered on the device where it is registered. It’s like the “Two-man rule” for launching nuclear missiles in war movies—the system will not function if both people are not present to turn the key.
- Risk-based authentication, or passive factor authentication, could allow you to create a scalable solution. You could adjust the security based on the sensitivity of the data you want to access. For example, you might want Spotify to automatically log you in when connected to your home Wi-Fi network, but then require your bank to verify that you are on a device you own in conjunction with a thumb print.
- Text it and forget it? TextPower has developed a way to log in without needing a username or password. It may not be ideal for every situation, but it could be convenient for certain applications.
And finally…
- You might want to consider perfecting your duck-face for this one, because Amazon recently submitted a patent that would allow you to use a selfie as a password.
It’s not one size fits all
There is not one all-encompassing solution to the password problem. And the best solution can vary based on cost, sensitivity of data and tolerable error rates.
Still, it is recommended that you have a best practice in mind when setting your passwords. Simply increasing the complexity requirements for passwords is an exponential increase in security. Then, depending on the application or the environment, combine that password with two or more factors of authentication.
 If you are worried poor practices may have you exposed, head over to haveibeenpwned.com, and you can have your password information checked against any known data breeches.
If you are worried poor practices may have you exposed, head over to haveibeenpwned.com, and you can have your password information checked against any known data breeches.
History, and logic, says the password should be dead by now. It seems though, that—just like a zombie outbreak—they are nearly everywhere you look. It makes sense to increase your defenses, and evaluate your current authentication methods (personal and business) to find out if you’re using the best configuration for your needs.
…Oh, and now would also probably be a good time to change your password to something a little more unique than…password.
